Updated on 05/19/20 with clarification and links to various KBs for further details on this setup.
About a few months ago, I wrote about Blackberry UEM User Self-Service Portal. VMware AirWatch / Workspace ONE offers Self-Service Portal as well, and I will now share details of the setup and the self-service portal.
What I won’t do just yet is to compare VMware AirWatch / Workspace ONE with Blackberry UEM. I’m still somewhat biased toward AirWatch after working with the product more so than any other competitive product out there. After all, VMware AirWatch / Workspace ONE must be doing something right to remain as the leader in the digital workspace.
For this setup, you will find the links below from VMware relatively insightful.
- Self-Service Portal
- Self-Service Portal Actions Matrix
- Accessing the Self Service Portal on Devices
- Self-Service Portal (SSP) Login
- How to Customize the Self Service Portal
- Customizing options on the Self Service Portal
- Customizing SSP URL
Before users can access the self-service portal, there are a few pre-requisites in the web console.
First of all, we need to identify the URL for accessing the self-service portal. This can be found under GROUPS & SETTINGS -> All Settings -> System -> Advanced -> Site URLs. It should look something like this: https://Your_AirWatch_URL/MyDevice
Please note: Your Account Role must be at least the Account Administrator or above to access the Site URLs section.
You can also modify the URL by following the steps from this KB.
Next, we need to confirm the role assigned to the organization group(s). The default roles are located at ACCOUNTS -> Users -> Roles.
Clicking on any of the default roles will reveal the exact permissions assigned within the self-service portal. However, you will not be able to check or uncheck any of the boxes within the default roles.
You can also add a custom role and customize the permissions within accordingly. However, there is no option to clone any of the default roles and then customize it. Also, all the boxes within the custom role are already checked off making the task somewhat tedious especially if you only want to grant very limited permission to users.
Finally, we will assign whichever role applicable to users via GROUPS & SETTINGS -> All Settings -> Devices & Users -> General -> Enrollment -> Grouping -> Default Role (under Default). Then, click on the drop-down arrow and select the desired role. For this post, we will select Full Access to see all the features available to end-user within the self-service portal.
Optional: You can also change the login or authentication options by visiting GROUPS & SETTINGS -> All Settings -> Installation -> Advanced -> Other.
Please note: Your Account Role must be at least the AirWatch Administrator or above to access the Other section.
Once all the pre-requisites above are completed, your users will be ready to sign onto the self-service portal. Again, start by navigating to https://Your_AirWatch_URL/MyDevice
I asked VMware Workspace ONE technical support whether the wording should have been re-branded for the self-service portal. At the moment, it’s a no (or they don’t know and it still hasn’t changed in over a year.)
Oh no, it looks like something might still be missing or configured incorrectly.
After troubleshooting with VMware Workspace ONE technical support, this turns out to be an ID10T error on my side and a design flaw on the AirWatch side. The former can be easily fixed but not the latter.
Before writing this post, I did assign a custom role to the user group which my account was part of where access to SSP was denied. It turns out once a role is assigned to the group, changing it to another role under GROUPS & SETTINGS -> All Settings -> Devices & Users -> General -> Enrollment -> Grouping -> Default Role will not affect devices that are already enrolled.
The workaround, in this case, is to modify the User Role within the individual user account.
If we opt to make this change on multiple user accounts, the use of AirWatch API will be required which to me is a design flaw.
Once the issue above is resolved, we will be able to log in as the end-user to the self-service portal.
Check out the Self-Service Portal Actions Matrix for the complete list of actions permissible based on the specific platform. Keep in mind that the specific actions available are also limited by both the device ownership type (Employee-Owned versus Corporate-Owned) and user role (Basic Access, External Access, and Full Access.)
With the Full Access role, you should see all the options similar to the below.
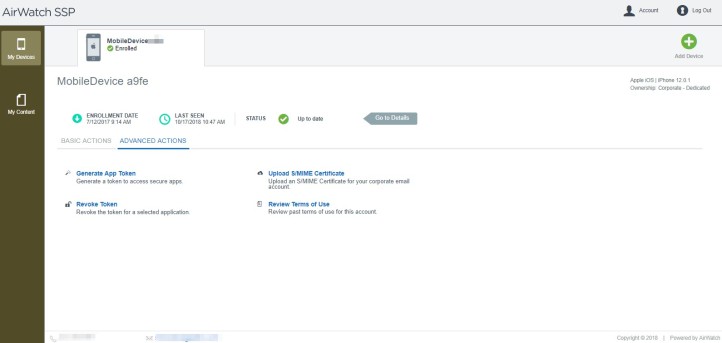
With the Basic Access role, you should see all the options similar to the below.


With the External Access role, you should see all the options similar to the below.
Clicking on Go to Details will reveal the below.
With either Full Access or Basic Access role assigned, the user can also register a new device within the portal.
With the right amount of training and communication to end-users, this self-service portal will sure help reduce the support call and allow admins more time to implement new features and settings in VMware Workspace ONE.
In a future post, I will take this setup to the next level with Single Sign-on leveraging Workspace ONE Access (formerly known as VMware Identity Manager.). Stay tuned!
Configuring Single Sign-on from the VMware Identity Manager Service to AirWatch Applications















[…] VMware Workspace ONE UEM by AirWatch Self-Service Portal … […]
LikeLike